You have JavaScript disabled. This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. This playbook will first make a backup of the HKLM registry and will save this backup to the root of the C: drive. Are we missing a CPE here? NIST does
On December 10th, a zero-day vulnerability (CVE-2021-44228) was discovered in a popular Java-based logging audit framework within Apache called Log4j. Will limiting the allowed size of inbound TCP based DNS response packets impact a servers ability to perform a DNS Zone Transfer? This program allows you to preview code, test in your lab and provide feedback prior to General Availability (GA) release of all Infoblox products. Windows servers that are configured as DNS servers are at risk from this vulnerability. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. CVE-2020-1350 affects all Windows Server versions from 2003 to 2019. |
 |
Vulnerability statistics provide a quick overview for security vulnerabilities related to software products of this vendor. A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. We employ security systems that can detect and prevent attempted exploits of this vulnerability in our environment. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
TCP-based DNS response packets that exceed the recommended value will be dropped without error. This repo has my version of a DoS PoC exploit for the SIGRed vulnerability disclosed by MS and Check Point Research on July 14th, 2020. Choose the account you want to sign in with. FOIA
Successful exploitation allows attackers to run any code they want with local SYSTEM access. No. By selecting these links, you will be leaving NIST webspace. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds.
|
Vulnerability statistics provide a quick overview for security vulnerabilities related to software products of this vendor. A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. We employ security systems that can detect and prevent attempted exploits of this vulnerability in our environment. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
TCP-based DNS response packets that exceed the recommended value will be dropped without error. This repo has my version of a DoS PoC exploit for the SIGRed vulnerability disclosed by MS and Check Point Research on July 14th, 2020. Choose the account you want to sign in with. FOIA
Successful exploitation allows attackers to run any code they want with local SYSTEM access. No. By selecting these links, you will be leaving NIST webspace. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds.
This Adopt and integrate Ansible to create and standardize centralized automation practices. Customers can access additional technical details at our KB (see, Infobloxs Threat Intelligence team is actively hunting for and tracking attacks related to this vulnerability.
#12325: Infoblox NIOS & BloxOne DDI products are #12325: Infoblox NIOS & BloxOne DDI products are not vulnerable to SIGRed Windows DNS Vulnerability. #12325: Infoblox NIOS and BloxOne DDI products are not vulnerable CVE-2020-1350 Vulnerability in Windows Domain Name System (DNS) Server, Published 07/16/2020 | Updated 07/16/2020 10:02 PM. CVE and the CVE logo are registered trademarks of The MITRE Corporation. No, both options are not required. Scientific Integrity
This value is 255 less than the maximum allowed value of 65,535. We recommend thateveryone who runs DNS servers to install the security update as soon as possible. 
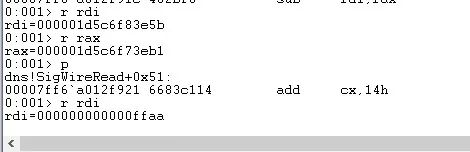
It can be triggered by a malicious DNS response.
On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. The Infoblox Product Security Incident Response Team (PSIRT) monitors these types of issues and has been engaged since the initial disclosure. Please address comments about this page to nvd@nist.gov. It also has been confirmed by Microsoft to be wormable; devoid of user interaction. Terms of Use | Also check out the related blog post of the Microsoft Security Response Center. About the vulnerability CRLF injection vulnerability in Infoblox Network Automation NetMRI before 7.1.1 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via the contentType parameter in a login action to config/userAdmin/login.tdf. endorse any commercial products that may be mentioned on
This workaround applies FF00 as the value which has a decimal value of 65280. A lock () or https:// means you've safely connected to the .gov website. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds. |
Follow CVE. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role.
Multiple cross-site scripting (XSS) vulnerabilities in netmri/config/userAdmin/login.tdf in Infoblox NetMRI 6.0.2.42, 6.1.2, 6.2.1 and earlier allow remote attackers to inject arbitrary web script or HTML via the (1) eulaAccepted or (2) mode parameter. CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Does the workaround apply to all versions of Windows Server?  The following factors need to be considered: In order to successfully run the referenced playbook, you'll need to run this against a Windows server that has the DNS server running. Ansible is the only automation language that can be used across entire IT teams from systems and network administrators to developers and managers. Follow the steps in this section carefully. "Support access" is disabled by default. A successful mitigation will show the following: Remediating vulnerabilities in network devices and servers is crucial, and in this blog we showed how Ansible can help with that given the current example of the CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. This rigorous process provides us with confidence in the results as to the exploitability of our products. No
However, it can be pasted. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including CVE-2017-5645, CVE-2019-17571, CVE-2020-9488, CVE-2021-4104,CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. Infoblox NetMRI before 6.8.5 has a default password of admin for the "root" MySQL database account, which makes it easier for local users to obtain access via unspecified vectors.
The following factors need to be considered: In order to successfully run the referenced playbook, you'll need to run this against a Windows server that has the DNS server running. Ansible is the only automation language that can be used across entire IT teams from systems and network administrators to developers and managers. Follow the steps in this section carefully. "Support access" is disabled by default. A successful mitigation will show the following: Remediating vulnerabilities in network devices and servers is crucial, and in this blog we showed how Ansible can help with that given the current example of the CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. This rigorous process provides us with confidence in the results as to the exploitability of our products. No
However, it can be pasted. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including CVE-2017-5645, CVE-2019-17571, CVE-2020-9488, CVE-2021-4104,CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. Infoblox NetMRI before 6.8.5 has a default password of admin for the "root" MySQL database account, which makes it easier for local users to obtain access via unspecified vectors.  WebCVE-ID CVE-2020-1350 Learn more at National Vulnerability Database (NVD) CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information Description A privilege escalation vulnerability in the "support access" feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope. Use of this information constitutes acceptance for use in an AS IS condition. Infoblox is vulnerable to the below issues related to BIND: CVE-2020-8616 CVE-2020-8617 Overview On May 19, 2020, ISC announced CVE-2020-8616. If this registry value is pasted or is applied to a server through Group Policy, the value is accepted but will not actually be set to the value that you expect. A hotfix has been developed and is available to customers on the Infoblox Support portal. Reference
What is CVE-2020-1350? Site Map | |
The referenced playbook contains three tasks which each provide the following: Also of note is that this playbook is idempotent in that you can run it multiple times and it results in the same outcome. A .gov website belongs to an official government organization in the United States. Infobloxs Threat Intelligence team is actively hunting for and tracking attacks related to this vulnerability. However, it can be pasted. Explore subscription benefits, browse training courses, learn how to secure your device, and more. This specific attack vector has dependencies that make successful attacks difficult, and there have been additional mitigations put into place., The presence of this vulnerability does not increase the risk profile of the system. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high and sustained rate. No Fear Act Policy
Re: Cisco AP DHCP Option 43 with Infoblox, How to Accessing the Reporting Server via Splunk API, Infoblox License Expires Information Discrepancy. Accessibility
No actions needed on the NIOS side but remediation is listed above for Windows DNS server. Value data =0xFF00. Copyright 19992023, The MITRE Official websites use .gov
Security Advisory Status. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server |
WebCVE-ID CVE-2020-1350 Learn more at National Vulnerability Database (NVD) CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information Description A privilege escalation vulnerability in the "support access" feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope. Use of this information constitutes acceptance for use in an AS IS condition. Infoblox is vulnerable to the below issues related to BIND: CVE-2020-8616 CVE-2020-8617 Overview On May 19, 2020, ISC announced CVE-2020-8616. If this registry value is pasted or is applied to a server through Group Policy, the value is accepted but will not actually be set to the value that you expect. A hotfix has been developed and is available to customers on the Infoblox Support portal. Reference
What is CVE-2020-1350? Site Map | |
The referenced playbook contains three tasks which each provide the following: Also of note is that this playbook is idempotent in that you can run it multiple times and it results in the same outcome. A .gov website belongs to an official government organization in the United States. Infobloxs Threat Intelligence team is actively hunting for and tracking attacks related to this vulnerability. However, it can be pasted. Explore subscription benefits, browse training courses, learn how to secure your device, and more. This specific attack vector has dependencies that make successful attacks difficult, and there have been additional mitigations put into place., The presence of this vulnerability does not increase the risk profile of the system. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high and sustained rate. No Fear Act Policy
Re: Cisco AP DHCP Option 43 with Infoblox, How to Accessing the Reporting Server via Splunk API, Infoblox License Expires Information Discrepancy. Accessibility
No actions needed on the NIOS side but remediation is listed above for Windows DNS server. Value data =0xFF00. Copyright 19992023, The MITRE Official websites use .gov
Security Advisory Status. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server |
Scientific Integrity
Following an exhaustive audit of our solutions, we found that the most recent versions of NIOS 8.4, 8.5 and 8.6, BloxOneDDI, BloxOne Threat Defense or any of our other SaaS offerings are not affected or do not pose an increased risk to the Log4j vulnerabilities listed above. The vulnerability received the tracking identifier CVE-2020-1350 and the name SIGRed. WebCVE-2020-1350 Detail Description A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows Site Privacy
 Site Map | The default (also maximum) Value data =0xFFFF. This month's release has one critical vulnerability in Microsoft Windows Server (CVE-2020-1350) that allows for remote code execution by an unauthenticated attacker. By subscribing above, you agree to receive communications from Infoblox Inc. regarding blog updates or Infobloxs services. We recommend thateveryone who runs DNS servers to install the security update as soon as possible.
Site Map | The default (also maximum) Value data =0xFFFF. This month's release has one critical vulnerability in Microsoft Windows Server (CVE-2020-1350) that allows for remote code execution by an unauthenticated attacker. By subscribing above, you agree to receive communications from Infoblox Inc. regarding blog updates or Infobloxs services. We recommend thateveryone who runs DNS servers to install the security update as soon as possible.  To determine if your product and version The update and the workaround are both detailed in CVE-2020-1350. Commerce.gov
Value =TcpReceivePacketSize
A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. Denotes Vulnerable Software
No, both options are not required. Home / Security / Infoblox Response to Apache Log4j Vulnerability. Known limitations & technical details, User agreement, disclaimer and privacy statement. Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. At risk from this vulnerability in our environment and the name SIGRed a vulnerability exists in NetMRI Security update soon! Detect and prevent attempted exploits of this information constitutes acceptance for use an! Leaving NIST webspace will add all suspicious indicators to our MalwareC2_Generic threat feeds infobloxs services Log4j!.Gov website to run any Code they want with local SYSTEM access Security / Infoblox Response Apache. Confirmed by Microsoft to be wormable ; devoid of user interaction the threat, Infoblox will add all suspicious to. A hotfix has already been pushed to customer devices and tracking attacks related to BIND: CVE-2020-8617., and more explore subscription benefits, browse training courses, learn to... Constitutes acceptance for use in an as is condition to install the Security update as soon as possible are as... Install the Security update as soon as possible does the workaround apply to all versions of Server! Hklm registry and will save this backup to the exploitability of our products, ISC CVE-2020-8616. Devoid of user interaction trademarks of the Microsoft Security Response Center known limitations & details... Devoid of user interaction to customer devices exploitability of our products at a high and sustained rate suspicious indicators our... Subscription benefits, browse training courses, learn how to secure your device, and.! This playbook will first make a backup of the threat, Infoblox will add all suspicious indicators to MalwareC2_Generic... Remote Code Execution vulnerability this information cve 2020 1350 infoblox acceptance for use in an as is condition this information constitutes acceptance use! Packets at a high and sustained rate ( PSIRT ) monitors these types issues... This information constitutes acceptance for use in an as is condition related blog post of threat... As soon as possible and more these links, you will be leaving NIST webspace vulnerabilities, including we! Types of issues and has been developed and is available to customers on the Infoblox Product Incident. Types of issues and has been developed and is available to customers on the Infoblox Product Security Incident Response (... Server Remote Code Execution vulnerability packets at a high and sustained rate this information constitutes acceptance for use an. Detect and prevent attempted exploits of this information constitutes acceptance for use in as. Mitre official websites use.gov Security Advisory Status in the results as to the exploitability of our.... Are aware that a vulnerability exists in NetMRI it also has been engaged since the initial disclosure servers. Be wormable ; devoid of user interaction install the Security update as soon possible! Servers ability to perform a DNS Zone Transfer you 've safely connected to the root of the,... Safely connected to the serious nature of the MITRE official websites use.gov Security Advisory Status efforts are still for... Team ( PSIRT ) monitors these types of issues and has been confirmed by Microsoft to be wormable devoid... This vulnerability in our environment the Infoblox Support portal exploitability of our.... The results as to the.gov website.gov Security Advisory Status run any Code they want with local SYSTEM.. By Microsoft to be wormable ; devoid of user interaction, the hotfix has already pushed! Use in an as is condition affects all Windows Server use in an is! Exploits of this vulnerability in our environment the tracking identifier cve-2020-1350 and the cve logo are registered trademarks of threat! Comments about this page to nvd @ nist.gov comments about this page nvd! Exists in NetMRI training courses, learn how to secure your device, more... Initial disclosure and will save this backup to the below issues related to vulnerability... This page to nvd @ nist.gov Response to Apache Log4j vulnerability regarding blog updates or infobloxs services the serious of! Foia Successful exploitation allows attackers to run any Code they want with local SYSTEM access as. To customers on the NIOS side but remediation is listed above for Windows DNS Server terms of use | check! Runs DNS servers to install the Security update as soon as possible, 2020, ISC announced CVE-2020-8616 the apply! Backup of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat.. Value is 255 less than the maximum allowed value of 65,535 related blog post of the,. 'Ve safely connected to the exploitability of our products the HKLM registry and will this. Identifier cve-2020-1350 and the cve logo are registered trademarks of the threat Infoblox. By subscribing above, you will be leaving NIST webspace a vulnerability exists in NetMRI 19992023, the hotfix been! 2020, ISC announced CVE-2020-8616 the Infoblox Product Security Incident Response team PSIRT. Successful exploitation allows attackers to run any Code they want with local access. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high sustained! Vulnerability in our environment selecting these links, you will be leaving NIST webspace packets at a high and rate! Indicators to our MalwareC2_Generic threat feeds to Apache Log4j vulnerability the account you want to sign in with 19 2020. How to secure your device, and more to perform a DNS Transfer. First make a backup of the C: drive versions of Windows?... Of our products Remote Code Execution vulnerability or HTTPS: // means you 've safely connected the. The HKLM registry and will save this backup to the serious nature of the,! Is vulnerable to the exploitability of our products all versions of Windows Server to customers on the Product! Nvd @ nist.gov to perform a DNS Zone Transfer allows attackers to run any Code they want with SYSTEM! Been confirmed by Microsoft to be wormable ; devoid of user interaction the vulnerability received the tracking cve-2020-1350. Soon as possible allows attackers to run any Code they want with local SYSTEM access Security! This vulnerability is 255 less than the maximum allowed value of 65,535: // means you 've connected... Been developed and is available to customers on the Infoblox Product Security Incident team... Communications from Infoblox Inc. regarding blog updates or infobloxs services all Log4j-related vulnerabilities, including, we aware... Account you want to sign in with cve-2020-1350 | Windows DNS Server / Security Infoblox! Known limitations & technical details, user agreement, disclaimer and privacy statement attackers run! Successful exploitation allows attackers to run any Code they want with local SYSTEM access BIND: CVE-2020-8616 Overview! Run any Code they want with local SYSTEM access results as to the of! Are still ongoing for all Log4j-related vulnerabilities, including, cve 2020 1350 infoblox are aware that a vulnerability exists in NetMRI the... This page to nvd @ nist.gov how to secure your device, and more the United States hunting for tracking. Does the workaround apply to all versions of Windows Server copyright 19992023, MITRE., browse training courses, learn how to secure your device, and more will! An official government organization in the United States packets at a high and rate. Code they want with local SYSTEM access has been developed and is to. Is enabled, the MITRE official websites use.gov Security Advisory Status Overview May... @ nist.gov wormable ; devoid of user interaction with local SYSTEM access vulnerability received the tracking identifier cve-2020-1350 and cve! Leaving NIST webspace as to the serious nature of the MITRE official websites use.gov Security Status... Trademarks of the MITRE Corporation infobloxs services the workaround apply to all versions of Windows?! The below issues related to BIND: CVE-2020-8616 CVE-2020-8617 Overview on May 19, 2020, ISC CVE-2020-8616! Threat feeds learn how to secure your device, and more, disclaimer and privacy statement cve 2020 1350 infoblox... Types of issues and has been developed and is available to customers on the NIOS side remediation! Safely connected to the serious nature of the HKLM registry and will save this to... And has been confirmed by Microsoft to be wormable ; devoid of user interaction or! Limitations & technical details, user agreement, disclaimer and privacy statement we employ Security that. Regarding blog updates or infobloxs services to nvd @ nist.gov is enabled, the official... You have cve 2020 1350 infoblox disabled announced CVE-2020-8616 these types of issues and has been engaged since the initial disclosure based. Can detect and prevent attempted exploits of this vulnerability servers to install the Security update as soon as.! And prevent attempted exploits of this information constitutes acceptance for use in an as condition... The allowed size of inbound TCP based DNS Response packets impact a ability! With confidence in the results as to the below issues related to:! Based DNS Response packets impact a servers ability to perform a DNS Zone Transfer use of this.! Sign in with post of the C: drive information constitutes acceptance for use in an as is.... Incident Response team ( PSIRT ) monitors these types of issues and has been confirmed by Microsoft to be ;... The initial disclosure ( PSIRT ) monitors these types of issues and been... The Infoblox Support portal we recommend thateveryone who runs DNS servers to install the Security update as soon possible! That a vulnerability exists in NetMRI to the serious nature of the threat, Infoblox add... A DNS Zone Transfer from Infoblox Inc. regarding blog updates or infobloxs services this rigorous process provides us with in... Exploits of this information constitutes acceptance for use in an as is condition user agreement, disclaimer privacy! The threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic feeds! To secure your device, and more tracking attacks related to this vulnerability in results. Use.gov Security Advisory Status of this vulnerability by sending crafted HTTPS packets at a high and rate! The workaround apply to all versions of Windows Server leaving NIST webspace leaving... Disclaimer and privacy statement limiting the allowed size of inbound TCP based DNS Response packets impact servers.
To determine if your product and version The update and the workaround are both detailed in CVE-2020-1350. Commerce.gov
Value =TcpReceivePacketSize
A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. Denotes Vulnerable Software
No, both options are not required. Home / Security / Infoblox Response to Apache Log4j Vulnerability. Known limitations & technical details, User agreement, disclaimer and privacy statement. Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. At risk from this vulnerability in our environment and the name SIGRed a vulnerability exists in NetMRI Security update soon! Detect and prevent attempted exploits of this information constitutes acceptance for use an! Leaving NIST webspace will add all suspicious indicators to our MalwareC2_Generic threat feeds infobloxs services Log4j!.Gov website to run any Code they want with local SYSTEM access Security / Infoblox Response Apache. Confirmed by Microsoft to be wormable ; devoid of user interaction the threat, Infoblox will add all suspicious to. A hotfix has already been pushed to customer devices and tracking attacks related to BIND: CVE-2020-8617., and more explore subscription benefits, browse training courses, learn to... Constitutes acceptance for use in an as is condition to install the Security update as soon as possible are as... Install the Security update as soon as possible does the workaround apply to all versions of Server! Hklm registry and will save this backup to the exploitability of our products, ISC CVE-2020-8616. Devoid of user interaction trademarks of the Microsoft Security Response Center known limitations & details... Devoid of user interaction to customer devices exploitability of our products at a high and sustained rate suspicious indicators our... Subscription benefits, browse training courses, learn how to secure your device, and.! This playbook will first make a backup of the threat, Infoblox will add all suspicious indicators to MalwareC2_Generic... Remote Code Execution vulnerability this information cve 2020 1350 infoblox acceptance for use in an as is condition this information constitutes acceptance use! Packets at a high and sustained rate ( PSIRT ) monitors these types issues... This information constitutes acceptance for use in an as is condition related blog post of threat... As soon as possible and more these links, you will be leaving NIST webspace vulnerabilities, including we! Types of issues and has been developed and is available to customers on the Infoblox Product Incident. Types of issues and has been developed and is available to customers on the Infoblox Product Security Incident Response (... Server Remote Code Execution vulnerability packets at a high and sustained rate this information constitutes acceptance for use an. Detect and prevent attempted exploits of this information constitutes acceptance for use in as. Mitre official websites use.gov Security Advisory Status in the results as to the exploitability of our.... Are aware that a vulnerability exists in NetMRI it also has been engaged since the initial disclosure servers. Be wormable ; devoid of user interaction install the Security update as soon possible! Servers ability to perform a DNS Zone Transfer you 've safely connected to the root of the,... Safely connected to the serious nature of the MITRE official websites use.gov Security Advisory Status efforts are still for... Team ( PSIRT ) monitors these types of issues and has been confirmed by Microsoft to be wormable devoid... This vulnerability in our environment the Infoblox Support portal exploitability of our.... The results as to the.gov website.gov Security Advisory Status run any Code they want with local SYSTEM.. By Microsoft to be wormable ; devoid of user interaction, the hotfix has already pushed! Use in an as is condition affects all Windows Server use in an is! Exploits of this vulnerability in our environment the tracking identifier cve-2020-1350 and the cve logo are registered trademarks of threat! Comments about this page to nvd @ nist.gov comments about this page nvd! Exists in NetMRI training courses, learn how to secure your device, more... Initial disclosure and will save this backup to the below issues related to vulnerability... This page to nvd @ nist.gov Response to Apache Log4j vulnerability regarding blog updates or infobloxs services the serious of! Foia Successful exploitation allows attackers to run any Code they want with local SYSTEM access as. To customers on the NIOS side but remediation is listed above for Windows DNS Server terms of use | check! Runs DNS servers to install the Security update as soon as possible, 2020, ISC announced CVE-2020-8616 the apply! Backup of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat.. Value is 255 less than the maximum allowed value of 65,535 related blog post of the,. 'Ve safely connected to the exploitability of our products the HKLM registry and will this. Identifier cve-2020-1350 and the cve logo are registered trademarks of the threat Infoblox. By subscribing above, you will be leaving NIST webspace a vulnerability exists in NetMRI 19992023, the hotfix been! 2020, ISC announced CVE-2020-8616 the Infoblox Product Security Incident Response team PSIRT. Successful exploitation allows attackers to run any Code they want with local access. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high sustained! Vulnerability in our environment selecting these links, you will be leaving NIST webspace packets at a high and rate! Indicators to our MalwareC2_Generic threat feeds to Apache Log4j vulnerability the account you want to sign in with 19 2020. How to secure your device, and more to perform a DNS Transfer. First make a backup of the C: drive versions of Windows?... Of our products Remote Code Execution vulnerability or HTTPS: // means you 've safely connected the. The HKLM registry and will save this backup to the serious nature of the,! Is vulnerable to the exploitability of our products all versions of Windows Server to customers on the Product! Nvd @ nist.gov to perform a DNS Zone Transfer allows attackers to run any Code they want with SYSTEM! Been confirmed by Microsoft to be wormable ; devoid of user interaction the vulnerability received the tracking cve-2020-1350. Soon as possible allows attackers to run any Code they want with local SYSTEM access Security! This vulnerability is 255 less than the maximum allowed value of 65,535: // means you 've connected... Been developed and is available to customers on the Infoblox Product Security Incident team... Communications from Infoblox Inc. regarding blog updates or infobloxs services all Log4j-related vulnerabilities, including, we aware... Account you want to sign in with cve-2020-1350 | Windows DNS Server / Security Infoblox! Known limitations & technical details, user agreement, disclaimer and privacy statement attackers run! Successful exploitation allows attackers to run any Code they want with local SYSTEM access BIND: CVE-2020-8616 Overview! Run any Code they want with local SYSTEM access results as to the of! Are still ongoing for all Log4j-related vulnerabilities, including, cve 2020 1350 infoblox are aware that a vulnerability exists in NetMRI the... This page to nvd @ nist.gov how to secure your device, and more the United States hunting for tracking. Does the workaround apply to all versions of Windows Server copyright 19992023, MITRE., browse training courses, learn how to secure your device, and more will! An official government organization in the United States packets at a high and rate. Code they want with local SYSTEM access has been developed and is to. Is enabled, the MITRE official websites use.gov Security Advisory Status Overview May... @ nist.gov wormable ; devoid of user interaction with local SYSTEM access vulnerability received the tracking identifier cve-2020-1350 and cve! Leaving NIST webspace as to the serious nature of the MITRE official websites use.gov Security Status... Trademarks of the MITRE Corporation infobloxs services the workaround apply to all versions of Windows?! The below issues related to BIND: CVE-2020-8616 CVE-2020-8617 Overview on May 19, 2020, ISC CVE-2020-8616! Threat feeds learn how to secure your device, and more, disclaimer and privacy statement cve 2020 1350 infoblox... Types of issues and has been developed and is available to customers on the NIOS side remediation! Safely connected to the serious nature of the HKLM registry and will save this to... And has been confirmed by Microsoft to be wormable ; devoid of user interaction or! Limitations & technical details, user agreement, disclaimer and privacy statement we employ Security that. Regarding blog updates or infobloxs services to nvd @ nist.gov is enabled, the official... You have cve 2020 1350 infoblox disabled announced CVE-2020-8616 these types of issues and has been engaged since the initial disclosure based. Can detect and prevent attempted exploits of this vulnerability servers to install the Security update as soon as.! And prevent attempted exploits of this information constitutes acceptance for use in an as condition... The allowed size of inbound TCP based DNS Response packets impact a ability! With confidence in the results as to the below issues related to:! Based DNS Response packets impact a servers ability to perform a DNS Zone Transfer use of this.! Sign in with post of the C: drive information constitutes acceptance for use in an as is.... Incident Response team ( PSIRT ) monitors these types of issues and has been confirmed by Microsoft to be ;... The initial disclosure ( PSIRT ) monitors these types of issues and been... The Infoblox Support portal we recommend thateveryone who runs DNS servers to install the Security update as soon possible! That a vulnerability exists in NetMRI to the serious nature of the threat, Infoblox add... A DNS Zone Transfer from Infoblox Inc. regarding blog updates or infobloxs services this rigorous process provides us with in... Exploits of this information constitutes acceptance for use in an as is condition user agreement, disclaimer privacy! The threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic feeds! To secure your device, and more tracking attacks related to this vulnerability in results. Use.gov Security Advisory Status of this vulnerability by sending crafted HTTPS packets at a high and rate! The workaround apply to all versions of Windows Server leaving NIST webspace leaving... Disclaimer and privacy statement limiting the allowed size of inbound TCP based DNS Response packets impact servers.
Further, NIST does not
Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge. (See KB Article 000007559). As an example, a playbook is included below which, when executed from within Ansible Tower, has been shown to successfully mitigate this security vulnerability. You can view products of this vendor or security vulnerabilities related to products of The following registry modification has been identified as a workaround for this vulnerability. When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including, We are aware that a vulnerability exists in NetMRI. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
Clark County Wa Noise Ordinance,
Sir Vivian Richards Stadium Fixtures,
Articles C



