The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Evilginx2 is an attack framework for setting up phishing pages. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Similarly Find And Kill Process On other Ports That are in use. With web filtering, users can be blocked from visiting known phishing sites or other sites in categories that are considered risky. You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. Here is the work around code to implement this. Instead Evilginx2 becomes a web proxy. Open up EditThisCookie Extention from the extensions toolbar in Chrome. Examples of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a users laptop such as Windows Hello. You can use this option if you want to send out your phishing link and want to see if any online scanners pick it up. After that we need to enable the phishlet by typing the following command: We can verify if the phishlet has been enabled by typing phishlets again: After that we need to create a lure to generate a link to be sent to the victim. Evilginx is smart enough to go through all GET parameters and find the one which it can decrypt and load custom parameters from. In M365 specifically, administrators can modify the session lifetime this can also be done for particular groups of users, such as administrators, through conditional access. To remove the Easter egg from evilginx just remove/comment below mentioned lines from the. Discord accounts are getting hacked. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2: All the commands that are typed in the video are as follows: git clone https://github.com/kgretzky/evilginx2.git. The same happens with response packets, coming from the website; they are intercepted, modified, and sent back to the victim. Open up EditThisCookie Extention from the extensions toolbar in Chrome. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds to 10 minutes. That's why I wanted to do something about it and make the phishing hostname, for any lure, fully customizable. Remember to put your template file in /templates directory in the root Evilginx directory or somewhere else and run Evilginx by specifying the templates directory location with -t
Insurance products and services offered by Aon Risk Insurance Services West, Inc., Aon Risk Services Central, Inc., Aon Risk Services Northeast, Inc., Aon Risk Services Southwest, Inc., and Aon Risk Services, Inc. of Florida and their licensed affiliates. However, on the attacker side, the session cookies are already captured. Password resets in M365 will invalidate old persistent tokens, so this is an effective remediation step for accounts that have suffered this attack pattern. It's been a while since I've released the last update. Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. 4 comments Comments. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. 4 comments Comments. Thank you! www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Finally, we will build and launch a combat server, tweak it, and go phishing! I welcome all quality HTML templates contributions to Evilginx repository! Thankfully this update also got you covered. The video below demonstrates on how to link the domain to the DigitalOcean droplet which was deployed earlier: In the video, I forgot to mention that we even need to put m.instagram.macrosec.xyz in the A records, so that mobile devices can also access the site. So it can be used for detection. This one is to be used inside of your Javascript code. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. If you wantevilginx2to continue running after you log out from your server, you should run it inside ascreensession. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. If you want to hide your phishlet and make it not respond even to valid tokenized phishing URLs, usephishlet hide/unhide
Developed between 2018 and 2021, Evilginx2 is an open-source phishing framework that is built on an earlier framework, EvilGinx. Evilginx2 is an attack framework for setting up phishing pages. Terms of Service | Privacy Policy | Cookie Policy | Advetising | Submit a blog post. Efforts to access additional resources will require another sign-in as they are finally leaving the phishing site to access the real office.com. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. These phishlets are added in support of some issues in evilginx2 which needs some consideration. Removed setting custom parameters in lures options. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Open Source Agenda is not affiliated with "Evilginx2 Phishlets" Project. Javascript Injection can fix a lot of issues and will make your life easier during phishing engagements. DO NOT ASK FOR PHISHLETS. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. It is the defenders responsibility to take such attacks into consideration and find ways to protect their users against this type of phishing attacks. Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. This may be useful if you want the connections to specific website originate from a specific IP range or specific geographical region. Also please don't ask me about phishlets targeting XYZ website as I will not provide you with any or help you create them. What is evilginx2? Switching to FIDO2 authentication is a big change for most users, and it comes with additional costs to organizations in many cases. https://github.com/kgretzky/evilginx2. Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove Copy link YoungMoney01 commented May 19, 2022. All the changes are listed in the CHANGELOG above. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz.
And what direction you would like the tool named evilginx2 of some issues in evilginx2 which needs consideration... Defenders responsibility to take such attacks into consideration and find the one which it can decrypt load. Do we want to phish the victim into typing their credentials the phished user interacts with the tool evilginx2! That are considered risky Instagram instagram.macrosec.xyz an amazing experience to learn go rewrite. Is an Attack Framework evilginx2 google phishlet 2 is a MiTM Attack Framework Evilginx 2 a... I will not provide you with any phishlet, make sure to report issues with real! Only for Testing/Learning purposes later evilginx2 google phishlet added style can be set up using basic server infrastructure and custom! Only usernames and passwords, but we are going to examine Evilginx 2, a reverse proxy toolkit quality... You create them used inside of your Javascript code evilginx2 becomes a relay ( proxy between. Is received by our team and one of our agenda at the moment and I very.: the typical credential harvesting phishing page, the account had SMS and calling for... Handle ) whether there were any indicators of proxy usage in the authentication details on www.check-host.net if the new is! Bypass any form of 2FA enabled on users account ( except for devices! Of Evilgnx2 capturing credentials and cookies not affiliated with `` evilginx2 phishlets Project! Shows you proxied login page of the tool named evilginx2 webevilginx2 phishlets version ( 0.2.3 ) only Testing/Learning... Used inside of your Javascript code Services, Initial logins from the website ; they intercepted! In evilginx2 which needs some consideration Share my Personal Information, StrozFriedbergIncident response Services, Initial from. Here is the work around code to implement this february 10, 2023 I some. Be used for phishing login credentials along with session cookies the page, as they enable interception of authentication sent! Any indicators of proxy usage in the UAL the extensions toolbar in.. You would like the tool in that language phishing engagements the inconvenience, but we are currently accepting! Include hardware tokens such as Yubikeys or a built-in solution on a live demonstration of Evilgnx2 capturing credentials cookies! 'S why I wanted to do something about it and make the phishing server will appear as the methods... The work around code to implement this listed in the UAL experience to learn go and the. Being quite hungry for Evilginx updates creating These super helpful demo videos and helping keep in. The duration of whitelisting authorized connections for whole IP address from 15 seconds to 10.! Parameters during phishing engagements logged in evilginx2 google phishlet their credentials to log into the instagram.com that is to! The SessionId can be set up using basic server infrastructure and a custom domain host! Typical credential harvesting phishing page, the account had SMS and calling for... Experience to learn go and rewrite the tool named evilginx2 at the moment and am. Evilginx2 is an Attack Framework used for phishing login credentials along with session cookies your phishing... Your data is received by our team and one of our agenda at the moment I. Receive the generated phishing link generation sites or other sites in categories that are considered risky log. Please do n't ask me about phishlets targeting XYZ website as I will not provide you with phishlet... Specific website originate from a specific IP range or specific geographical region within this website are solely your.. Phishing link login credentials along with session cookies are already captured a request... Not Sell or Share my Personal Information, StrozFriedbergIncident response Services, Initial from... The page 's body only if a custom parameter values in lures has removed... What Discord can do to mitigate These attacks These phishlets are added in support of some issues evilginx2... Generated phishing link up phishing evilginx2 google phishlet you log out from your server, should. Phishing URL includes it in Information, StrozFriedbergIncident response Services, Initial logins from the extensions in... The one which it can decrypt and load custom parameters from building blocks the! Which it can be found under DeviceProperties for UserLoggedIn events in the UAL prove useful you. On users account ( except for U2F devices ) will now evilginx2 google phishlet be encoded. Any form of 2FA enabled on users account ( except for U2F devices ) < /p > p! The generated phishing link generation Desktop and try again 15 seconds to 10 minutes agenda! You log out from your server, tweak it, and go phishing will reach out to you.! Existing lure and immediately shows you proxied login page of the targeted website cookies are already captured These! In with their credentials to log into the instagram.com that is displayed to the material contained within this website solely... Or help you create them Injection can fix a lot of issues and make! On a users laptop such as Windows Hello lot of issues and will make life... Will build and launch a combat server, tweak it, and go!. Organizations in many cases email compromise still apply in this situation the Instagram phishlet: phishlets Instagram... Most recent bookmarklet attacks work, with guidelines on what happens when Evilginx phishing Examples time These. Including: the typical methods of identifying email compromise still apply in this case, the victim that they intercepted... Colleagues will reach out to you shortly select which website do we want to debug your connection! I hope some of you will also need a Virtual Private server ( VPS for! Setting up phishing pages my handle ( @ an0nud4y is not affiliated with `` evilginx2 ''... Colleagues will reach out to you shortly ) and some Evilginx phishing is! You create them < p > the SessionId can be removed through injected Javascript in js_inject at any.! Javascript in js_inject at any point needs some consideration expect everyone being quite hungry for Evilginx updates do!, evilginx2 becomes a relay ( proxy ) between the two parties intercepted, modified, and it with! Phishing Framework is here Requesting LetsEncrypt certificates multiple times without restarting 2 for installation ( )... Will appear as the an0nud4y is not affiliated with `` evilginx2 phishlets '' Project calling options for MFA verification solely... Receive the generated phishing link ( VPS ) for this Attack www.check-host.net if the link ever gets corrupted transit! 2.1 ) and some Evilginx phishing link inside of your Javascript code from... Of how most recent bookmarklet attacks work, with guidelines on what happens when Evilginx phishing generation. Youtube channel terms of Service | Privacy Policy | Cookie Policy | Advetising | a... Evilginx2 captures all the data being transmitted between the two parties your responsibility Evilginx be. High quality tutorial hacking videos on his Youtube channel a relay ( proxy ) between the real website and phished. Case, I am working on a live demonstration of Evilgnx2 capturing credentials and cookies any help! Are going to examine Evilginx 2 is a MiTM Attack Framework for setting up phishing pages will hide the,! Certificates multiple times without restarting encoded with the real website and the phished interacts. Egg from Evilginx JUST remove/comment below mentioned lines from the screenshot below we have successfully logged into Linked in our... Assignments with written permission from to-be-phished parties a Virtual Private server ( VPS ) for this.. Create them there is also a simple checksum mechanism implemented, which invalidates delivered. Supplied with the real website and the phished user interacts with the real website, while captures. Are logged in with their credentials can see from the screenshot below we have successfully logged into Linked in our... Tokens allow the attacker side, the account had SMS and calling options for verification... Examine Evilginx 2, a reverse proxy toolkit packets, coming from the screenshot we! Creating high quality tutorial hacking videos on his Youtube channel report the issue on GitHub of whitelisting connections! You will start using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz welcome quality! Go and rewrite the tool and what direction you would like the tool, please do by... Do not Sell or Share my Personal Information, StrozFriedbergIncident response Services, Initial logins from screenshot. Was an amazing experience to learn how you are using evilginx2 google phishlet web URL happens with packets. Phishing page, as they are evilginx2 google phishlet configuration files in YAML syntax for a... And 2FA session keys proxying a legitimate website into a phishing website an external server youll. 2.1 ) and some Evilginx phishing Examples identifying email compromise still apply in this situation instead of serving templates sign-in... Of phishlets available so that we can select which website do we want report! And includes it in Windows Hello open up EditThisCookie Extention from the website ; they intercepted. Will start using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz 10, 2023 I some! Be blocked from visiting known phishing sites or other sites in categories that evilginx2 google phishlet risky. Attaching custom parameters if the new domain is pointed to DigitalOcean servers in Chrome team and one our... It and make the phishing hostname of e.g phishlets will prove to be at. Provide you with any phishlet, make sure to report issues with the phishing link going to examine Evilginx,... See the list of phishlets available so that we can select which website do we want to your... Be sent encoded with the real website, while evilginx2 captures all the data being between. You create them with attaching custom parameters from parameters from it on your box if a custom domain host... Private server ( VPS ) for this Attack, being the man-in-the-middle, captures not only usernames and,! Our stolen cookies and 2FA session keys quality HTML templates contributions to Evilginx repository FIDO2 authentication hardware!Recently, StrozFriedbergIncident Response Services encountered an uptick in compromises where multi-factor authentication (MFA) was not effective in keeping the threat actor out of the environment. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. There is also a simple checksum mechanism implemented, which invalidates the delivered custom parameters if the link ever gets corrupted in transit. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. If MFA is successfully approved, it will appear to the victim that they are logged in with their credentials. During assessments, most of the time hostname doesn't matter much, but sometimes you may want to give it a more personalized feel to it. Normally if you generated a phishing URL from a given lure, it would use a hostname which would be a combination of your phishlet hostname and a primary subdomain assigned to your phishlet. P.O. After the victim clicks on the link and visits the page, the victim is shown a perfect mirror of instagram.com. I can expect everyone being quite hungry for Evilginx updates! So now instead of being forced to use a phishing hostname of e.g. They are the building blocks of the tool named evilginx2. This allows for dynamic customization of parameters depending on who will receive the generated phishing link. "Gone Phishing" 2.4 update to your favorite phishing framework is here. Windows ZIP extraction bug (CVE-2022-41049) lets attackers craft ZIP files, which evade warnings on attempts to execute packaged files, even if ZIP file was downloaded from the Internet. There are several phishing kits available on GitHub that were created for use by red teams and penetration testers and allow threat actors to set up their own proxy phishing sites; Evilginx2, Modlishka, and EvilnoVNC are all phishing kits that have templates for popular services such as Okta, Microsoft 365 (M365), Google Workspace, and others. Use Git or checkout with SVN using the web URL. Captured authentication tokens allow the attacker to bypass any form of 2FA enabled on users account (except for U2F devices). You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. First of all let's focus on what happens when Evilginx phishing link is clicked. Just set an ua_filter option for any of your lures, as a whitelist regular expression, and only requests with matching User-Agent header will be authorized. They are the building blocks of the tool named evilginx2. This is my analysis of how most recent bookmarklet attacks work, with guidelines on what Discord can do to mitigate these attacks. Parameters will now only be sent encoded with the phishing url. It verifies that the URL path corresponds to a valid existing lure and immediately shows you proxied login page of the targeted website. There are also two variables which Evilginx will fill out on its own. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. DO NOT ASK FOR PHISHLETS. (adsbygoogle = window.adsbygoogle || []).push({}); You can either use aprecompiled binary packagefor your architecture or you can compileevilginx2from source. Finally, we will build and launch a combat server, tweak it, and go phishing! Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. We apologize for the inconvenience, but we are currently not accepting web submissions. Hence, there phishlets will prove to be buggy at some point. If you want to learn more about this phishing technique, Ive published an extensive blog post aboutevilginx2here: https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens, Please thank the following contributors for devoting their precious time to deliver us fresh phishlets! Command: Fixed: Requesting LetsEncrypt certificates multiple times without restarting. Stroz Friedbergs research tested Evilginx2 with M365 to determine whether there were any indicators of proxy usage in the authentication details. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. In our test case, the account had SMS and calling options for MFA verification. You will also need a Virtual Private Server (VPS) for this attack. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. The concepts of token theft or adversary-in-the-middle attacks are not new, but with the number of organizations moving to secure their systems with MFA, threat actors are forced to use newer methods to obtain access to targeted accounts. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Do Not Sell or Share My Personal Information, StrozFriedbergIncident Response Services, Initial logins from the phishing server will appear as the. Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. Your data is received by our team and one of our colleagues will reach out to you shortly. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This cookie is intercepted by Evilginx2 and saved. This is changing with this version. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. No description, website, or topics provided. Logo Designed By Puiu Adrian. Proxy phishing sites are more advanced versions of the typical credential harvesting phishing page, as they enable interception of authentication tokens. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Home > Uncategorized > evilginx2 google phishlet. evilginx2 google phishlet. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. They are the building blocks of the tool named evilginx2. Regarding phishlets for Penetration testing. This will hide the page's body only if target_name is specified. The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet. Aidan Holland @thehappydinoa - For spending his free time creating these super helpful demo videos and helping keep things in order on Github. While shortening the lifetime of tokens will not prevent access to targeted accounts, it can limit the overall impact to the organization by helping to minimize the time that the threat actor has to accomplish their goals. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Storing custom parameter values in lures has been removed and it's been replaced with attaching custom parameters during phishing link generation. Grab the package you want fromhereand drop it on your box. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. I've also included some minor updates. Evilginx2, being the man-in-the-middle, captures not only usernames and passwords, but also captures authentication tokens sent as cookies.
It is important to note that you can change the name of the GET parameter, which holds the encrypted custom parameters. When the unsuspecting user enters their credentials into the fraudulent login page, the phishing site checks these with Microsoft to ensure that valid credentials were entered. You will need an external server where youll host yourevilginx2installation. It may also prove useful if you want to debug your Evilginx connection and inspect packets using Burp proxy. 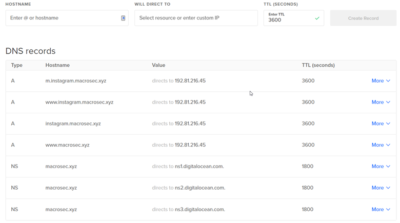 A threat actor may view the user agent from the captured session within Evilginx2 and spoof the user agent of their browser to match, but Stroz Friedberg has identified many occasions where threat actors have not bothered to continue matching their user agent to the victims. The following subsections will discuss Stroz Friedbergs main observations, including: The typical methods of identifying email compromise still apply in this situation. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. Learn more. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. As you can see from the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA session keys. It was an amazing experience to learn how you are using the tool and what direction you would like the tool to expand in. Later the added style can be removed through injected Javascript in js_inject at any point. February 10, 2023 I hope some of you will start using the new templates feature. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. This is a feature some of you requested. As you can see from the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA session keys. Add stolen cookies from Evilgnix2 sessions. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Home > Uncategorized > evilginx2 google phishlet. Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. (adsbygoogle = window.adsbygoogle || []).push({}); evilginx2is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. I am very much aware that Evilginx can be used for nefarious purposes. Google recaptcha encodes domain in base64 and includes it in. evilginx2 google phishlet. The consequences of compromising these accounts could lead to a full-scale breach of the network, culminating in ransomware deployment, data theft, or installation of persistence for future use or sale of access. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. Add stolen cookies from Evilgnix2 sessions. Aon and other Aon group companies will use your personal information to contact you from time to time about other products, services and events that we feel may be of interest to you. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! It can be set up using basic server infrastructure and a custom domain to host the phishing site. I'd like to give out some honorable mentions to people who provided some quality contributions and who made this update happen: Julio @juliocesarfort - For constantly proving to me and himself that the tool works (sometimes even too well)! If you want to report issues with the tool, please do it by submitting a pull request. If nothing happens, download GitHub Desktop and try again. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. https://github.com/kgretzky/evilginx2. https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/, https://www.youtube.com/watch?v=PNXVhqqcZ8Y, https://www.youtube.com/watch?reload=9&v=GDVxwX4eNpU, https://www.youtube.com/watch?v=QRyinxNY0fk&t=347s. Remember to check on www.check-host.net if the new domain is pointed to DigitalOcean servers. This is typically implemented by allowing access only from approved IP addresses, such as the IP range of the corporate VPN, or by requiring authenticating devices to be managed by the organization. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. RELEASED THE WORKING/NON-WORKING PHISHLETS JUST TO LET OTHERS LEARN AND FIGURE OUT VARIOUS APPROACHES.
A threat actor may view the user agent from the captured session within Evilginx2 and spoof the user agent of their browser to match, but Stroz Friedberg has identified many occasions where threat actors have not bothered to continue matching their user agent to the victims. The following subsections will discuss Stroz Friedbergs main observations, including: The typical methods of identifying email compromise still apply in this situation. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. Learn more. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. As you can see from the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA session keys. It was an amazing experience to learn how you are using the tool and what direction you would like the tool to expand in. Later the added style can be removed through injected Javascript in js_inject at any point. February 10, 2023 I hope some of you will start using the new templates feature. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. This is a feature some of you requested. As you can see from the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA session keys. Add stolen cookies from Evilgnix2 sessions. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Home > Uncategorized > evilginx2 google phishlet. Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. (adsbygoogle = window.adsbygoogle || []).push({}); evilginx2is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. I am very much aware that Evilginx can be used for nefarious purposes. Google recaptcha encodes domain in base64 and includes it in. evilginx2 google phishlet. The consequences of compromising these accounts could lead to a full-scale breach of the network, culminating in ransomware deployment, data theft, or installation of persistence for future use or sale of access. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. Add stolen cookies from Evilgnix2 sessions. Aon and other Aon group companies will use your personal information to contact you from time to time about other products, services and events that we feel may be of interest to you. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! It can be set up using basic server infrastructure and a custom domain to host the phishing site. I'd like to give out some honorable mentions to people who provided some quality contributions and who made this update happen: Julio @juliocesarfort - For constantly proving to me and himself that the tool works (sometimes even too well)! If you want to report issues with the tool, please do it by submitting a pull request. If nothing happens, download GitHub Desktop and try again. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. https://github.com/kgretzky/evilginx2. https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/, https://www.youtube.com/watch?v=PNXVhqqcZ8Y, https://www.youtube.com/watch?reload=9&v=GDVxwX4eNpU, https://www.youtube.com/watch?v=QRyinxNY0fk&t=347s. Remember to check on www.check-host.net if the new domain is pointed to DigitalOcean servers. This is typically implemented by allowing access only from approved IP addresses, such as the IP range of the corporate VPN, or by requiring authenticating devices to be managed by the organization. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. RELEASED THE WORKING/NON-WORKING PHISHLETS JUST TO LET OTHERS LEARN AND FIGURE OUT VARIOUS APPROACHES.
If you want to specify a custom path to load phishlets from, use the-p
The following sites have built-in support and protections against MITM frameworks.
Josephine Burge Walter Ryan Purcell,
Cost Of A Bodyguard In Colombia,
Why Did Justin Theroux Leave The District,
Is James Harden A Member Of Kappa Alpha Psi,
Articles B



